DirtyCOW Server Erase
This little tool was developed to exploit a known vulnerability in a Perl script on a virtual machine we'd been handed in class.
An unsantized input field that stored the contents locally allowed for the passing of an entire PHP script via a textarea. I decided to go a bit crazy with my exploit (in that the assignment called only for PoC), and so integrated a privilege-escalation attack utilizing the DirtyCOW vulnerability into a neat little shell script. The end result is a one-click server erase that wipes the target server's filesystem (via rm -rf / as root).
The included PHP script allows for cURL file upload (it doesn’t have an HTML form) and changes behavior based on passed GET parameters, either uploading or executing the dirtyc0w program.
A modification to the dirtyc0w exploit - done by using the metasploit msfvenom utility and placing that payload as a replacement for the hex values in the original dityc0w source - allowed for piping the rm command and options to the generated root shell.
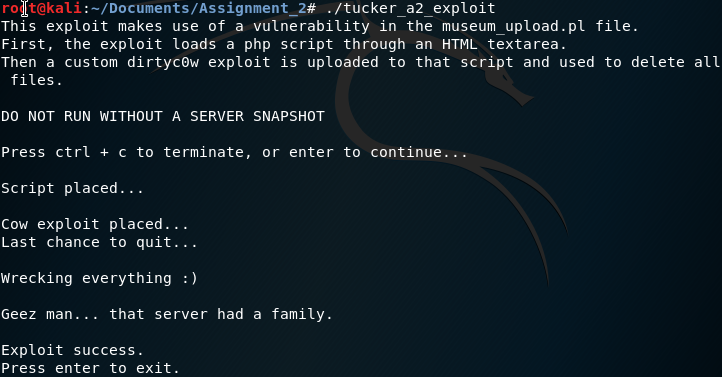
Above: The execution of the exploit
If you want to dig into the exploit: Download it here